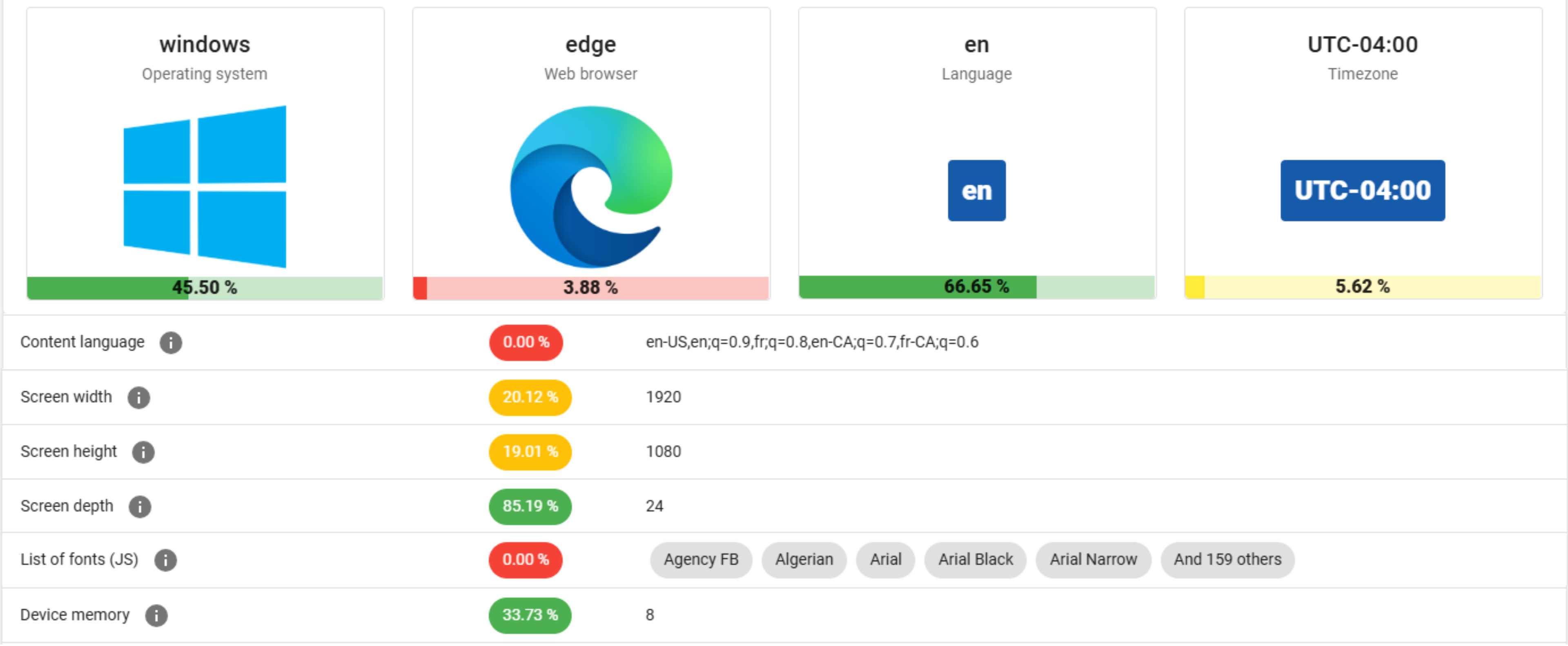
Amidst the glossy marketing for VPN services, it can be tempting to believe that the moment you flick on the VPN connection you can browse the internet with full privacy. Unfortunately this is quite far from the truth, as interacting with internet services like websites leaves a significant fingerprint. In a study by [RTINGS.com] this browser fingerprinting was investigated in detail, showing just how easy it is to uniquely identify a visitor across the 83 laptops used in the study.
As summarized in the related video (also embedded below), the start of the study involved the Am I Unique? website which provides you with an overview of your browser fingerprint. With over 4.5 million fingerprints in their database as of writing, even using Edge on Windows 10 marks you as unique, which is telling.
here is a fingerprinting test you can trust https://coveryourtracks.eff.org/
fingerprinting is nasty, i suggest canvas blocker extension because it gives them fake readouts
Also fingerprint.com
and creepjs https://abrahamjuliot.github.io/creepjs/
The only real advantage you gain is being able to watch things outside your region. Without lots of work, you’re pretty easily traceable on the modern internet.
The other major advantage is your ISP can’t build a profile on you. Considering they know who you are and where you live, that’s a pretty important air gap to me.
I remember in 1996 my neighbor was in one of these fancy new things on the internet called a “chat room”.
He got into an arguement with someone. It got heated. Until the other guy threatened to show up at my neighbors house.
My neighbor scoffed and laughed.
Then the guy put in my neighbors real address. To this day, that still scares me. And back then internet crime wasn’t taken seriously. In fact doxxing back then may not yet have even been a crime.
FYI:
https://www.thefire.org/research-learn/doxxing-free-speech-and-first-amendment
In the US, “doxxing” laws are pretty much state-by-state and many may be violating the first amendment.
Every time I use that site it says I am unique. So is that good? Surely if I was trackable, it would match me against the previous times I’d been there.
Or maybe the site is just spouting a load of clickbaity nonsense?
Yes, your browser is probably generating brand new canvas and other fingerprints every visit, which is a good thing.
Librewolf + uBlock Origin + Privacy Badger + containerise
For the comedy extra point, a user agent switcher can actively lie about your browser & OS.
Using a browser like Librewolf is, itself a unique identifier bc not enough people are using it.
EFF has a tool that lets you check your “uniqueness” and bc I used a lesser known browser, it was easier to track me.
Not that I mean you shouldn’t use it. I just wanted to clarify that it doesn’t make you safe from ads. :(
https://coveryourtracks.eff.org/ is the EFF tool.
My results say that I have strong protections against tracking, and that my browser is unique. It’s as good as I can get.
The agent switcher also tells the world my Librewolf on Linux is Chrome on Windows.
Isn’t it a bad thing to be unique in this context? If my browser is 1 in a million, that means that a tracker can pick me out of a lineup of a million users, no? That’s why a captcha can verify you as human simply by checking a box, because it can identify your unique browser as associated with human activity.
If I’m not mistaken, we want the opposite. We want our browsers to be as generic as possible if we don’t want to be tracked.
I would think unique means you appear as a never before seen individual and not one they can identify from their fingerprint history. If you fingerprint twice and both are unique, you are secure.
This somehow assumes that your fingerprint is going to vary, and be unique, every time you interact with a tracker. That’s basically not ever going to be the case for casual use.
If Cloudflare fails the tick-box Captcha and I need to tell it what squares contain motorcycles, that would suggest that I currently have a unique fingerprint that they do not have yet enough history on to tie to a person. How often do you get to do the square puzzle nowadays?
Thanks for linking it! I should have done that. And if LibreWolf is showing as Chrome on Windows, then you’re good!
Thanks for linking it! I should have done that. And if LibreWolf is showing as Chrome on Windows, then you’re good!
It should be noted that user agent switchers may break some website functionalities. I guess this is true for nearly all privacy protections, though this is the only one that gave me any noticeable trouble.
If the NSA wants you, they will get you. But I can hide from most of you with just a little email relay and a VPN
I can hide from everyone, I just walk into the woods.
Heeeeey. Former kid, current adult, and future crazy old man here. Quick question. Do they still have 1 box of communal porn in the woods? Every woods had one when I was a kid, but I haven’t been in the woods ever since we had to kill that bear.
Just wondering if woods porn is still a thing.
No, we’re more into woods erotic geocaching these days.
It’s always kind of funny when the Technology folks wade into well-researched and well-worn Privacy territory.
Do you want to not wave a giant flag of your activity to Google, Meta, MS, and your ISP when you do literally anything online? Either use a VPN and Mullvad (or Librewolf, but YMMV) browser, OR a VPN and Tor OR Tor with an https bridge if paying for a VPN will make you a target (Tor bridges are not for casuals, save them for those in genuine need).
VPN locations need to be changed. Frequently. Router level VPN at home becomes your “This is me” location, then make use of VPNs on each device when you want an extra layer of obfuscation.
There’s not a lot of middle ground at this point, and it’s not difficult.
Router level VPN at home becomes your “This is me” location
You and a thousand other people.
Yeah, but fingerprinting is effective by cross referencing.
There are 1,000 people with the IP 1.2.3.4
There are 500 people with the IP 1.2.3.4 using Firefox
There are 25 people with the IP 1.2.3.4 using Firefox with a 1440p screen
There are 2 people with the IP 1.2.3.4 using Firefox with the dark reader extension with a 1440p screen at 75Hz
etc.
So rotating the IP can screw with that.
Can they still not tell the screen’s size if you never fullsize your window? I 'member that advice from back in the day using Tor.
Does that mean my ISP can still detect if I’m going to websites they don’t approve of if I’m using Mullvad as my VPN but using Firefox as my browser?
Your ISP can’t tell who you are contacting if you are using a VPN, but websites will track you by other means.
No, with a VPN the only thing your ISP sees is you connecting to a VPN server IP.
But browser finger printing, on the other hand, can identify you to every website you visit, due to info your browser hands over to every website… Such as OS version, Resolution, installed Plugins, browser settings, geolocation info, etc…which is often unique enough to identify you out of the whole of the internet.
Ironically, locking your browser down with more security features/settings/plugins often makes you more identifiable. Cause capitalism is god damned sure they are gonna track you and monetize the hell out of your information, whether its via your name, your user name, or just your digital fingerprint.
Not your ISP. Google likely is the one following that. If you have uBlock Origin installed, click on the badge on any site and you’ll see which trackers there are. For Lemmy, it’s just going to list other lemmy instances. When you’re on that forbidden site, see if they have any Google analytics trackers - those are what will fingerprint you.
Then go to amiunique.org or hidemytracks.eff.org and see what information you’re giving up. Vanilla FF gives up fonts, sound card info, and graphics info, which are enough to pin you to specific hardware. If your machine isn’t extremely common, then Google knows it’s you.
Why not download the Mullvad browser? It’s free, and you’re paying for its development if you’re paying for the VPN.
I’ll give that a try, thank you!
Good luck I’m behind 7 proxies
I’m here with multi-hop VPN with the first two hops staying in-country and the rest all random + a shit load of DNS blocking lists and browser extensions + blocking Google. I use different VPN providers too. I’m also introducing variable delays to my traffic to make NetFilter data less helpful.
Please understand that browser extensions make you more easy to track. I used to be under the same assumption, but uBO is as far as you should go. fingerprints include your extensions.
My thinking is that most of the fingerprinting is happening by third parties, and where it’s the website operators themselves I’m not super concerned about being fingerprinted.
Look at the uBO trackers on each site and you’ll br surprised how often Google comes up.
From their domain that I’ve already blocked with DNS? Or are you talking about first-party scripts calling Google (which I’ve also seen though much more rare)?
In any case I block those too.
Google tag manager, which would be first party scripts now.
I bought a used laptop from a yard sale and only use public Wi-Fi and never use the laptop for anything with my name on it.
Pfft amateur, I break into my local Applbee’s after 2AM and use their POS terminal browser to look at used cars.
Applebee’s at 2AM which leaves a physical trail? Noob. I strap meshtastic nodes on wild dogs, using them as a Internet relay at 1-2kb a second, to look at manga leaks.
Does anyone know if Firefox’s claimed Anti fingerprinting technology is any good?
it’s useless. test it out with creepjs
This is why you use a separate browser for different activities and don’t cross contaminate.